Block 64 Network Access: How to open up ports on Windows Firewall via GPO
AD GPO Configuration Guide
Implementing this Group Policy Object (GPO) configuration allows seamless communication between the Block 64 server and devices on your network. This enables Block 64 to gather essential information about software, hardware, and resource utilization. Proper configuration ensures accurate data collection for your Block 64 application or Virtual Appliance.
Why Is This Important?
Even if your network uses external firewall solutions or the Windows Firewall is disabled, internal restrictions may prevent Block 64 from accessing necessary data.
This GPO setup resolves obstacles by opening essential ports, enabling seamless communication between the Block 64 server and network devices. It ensures uninterrupted data collection, allowing Block 64 to gather comprehensive information on software, hardware, and resource use. This is crucial in environments where internal restrictions may impede data access, even with external firewalls or a disabled Windows Firewall.
For comprehensive details on these configuration settings, please see the section GPO Settings: Configuration Details.
Step-by-Step Guide to Configure GPO for Block 64 Access
Follow these steps to configure the required GPO settings:
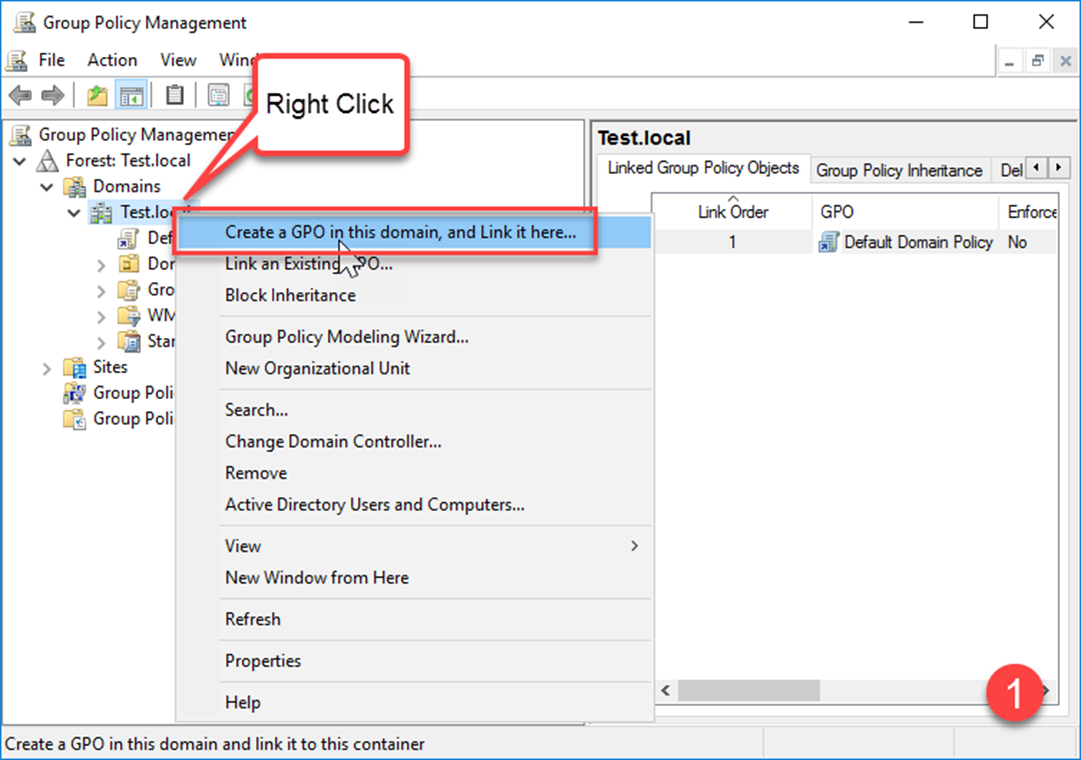
- Open Group Policy Management on your domain controller.
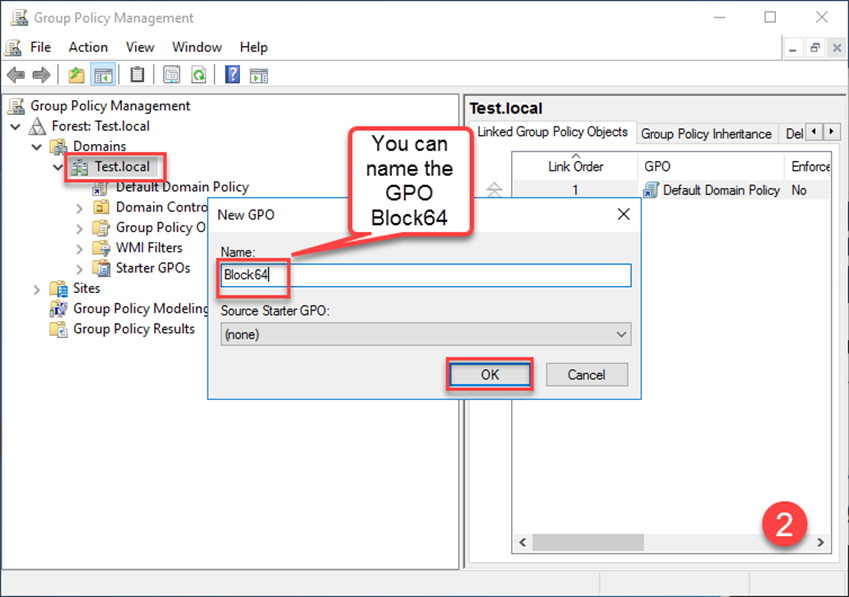
- Create a new Group Policy Object (GPO) and name it descriptively (e.g., "Block64-GPO").
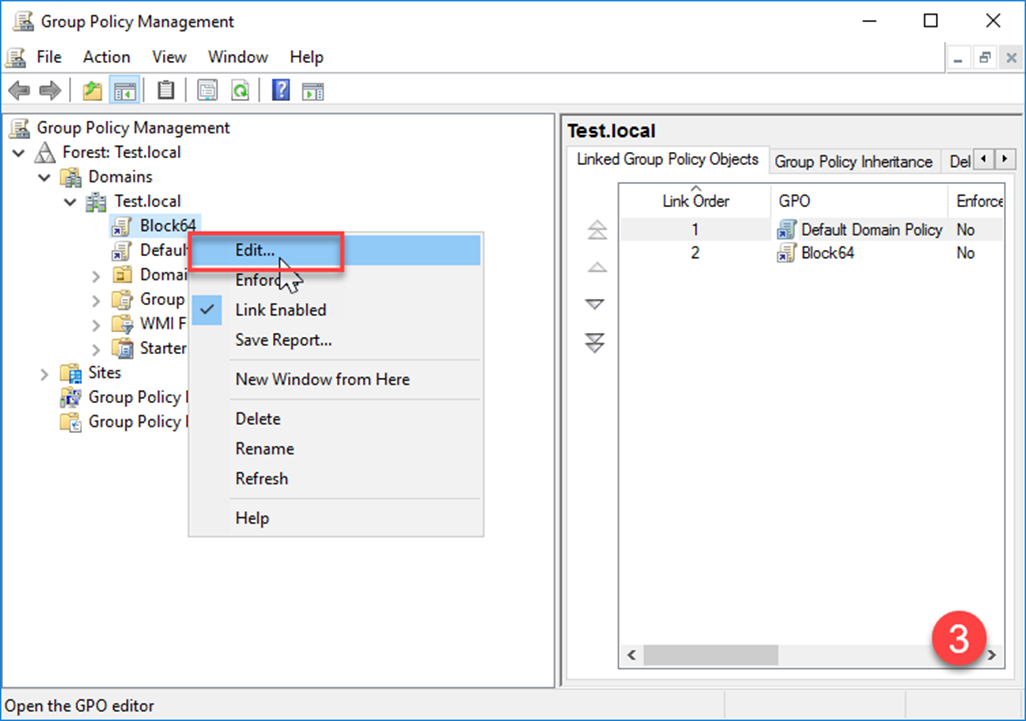
- Right-click the GPO and select Edit.
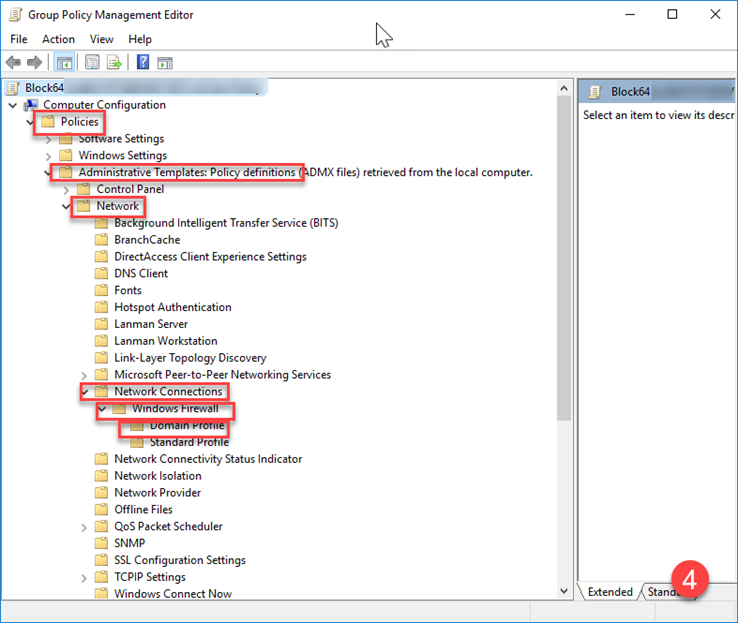
- Navigate to:
- Computer Configuration → Policies → Administrative Templates → Network → Network Connections → Windows Firewall → Domain Profile
- Computer Configuration → Policies → Administrative Templates → Network → Network Connections → Windows Firewall → Domain Profile
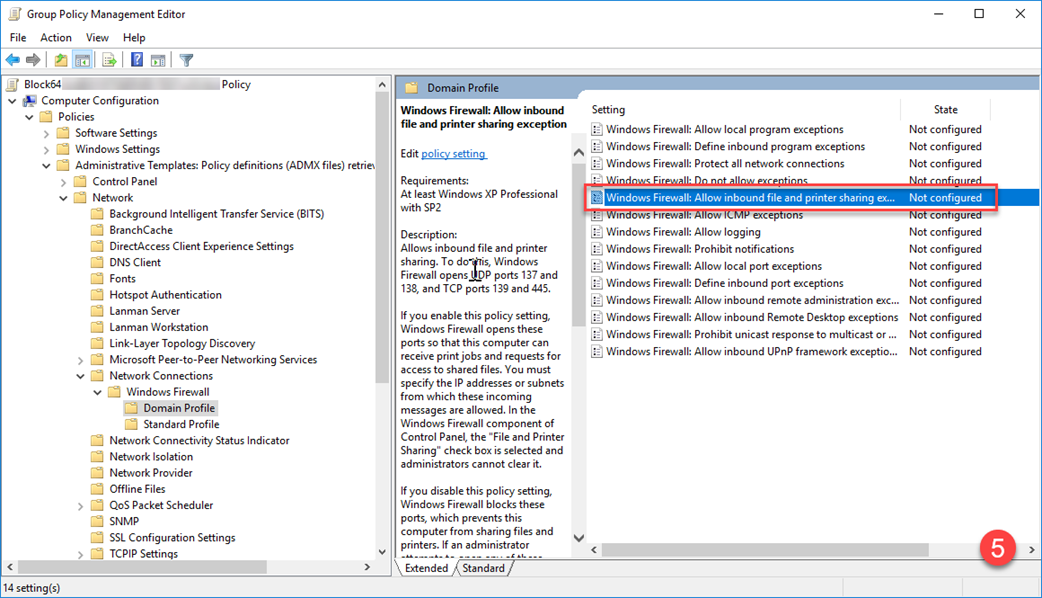
1. Configure File and Printer Sharing Exception
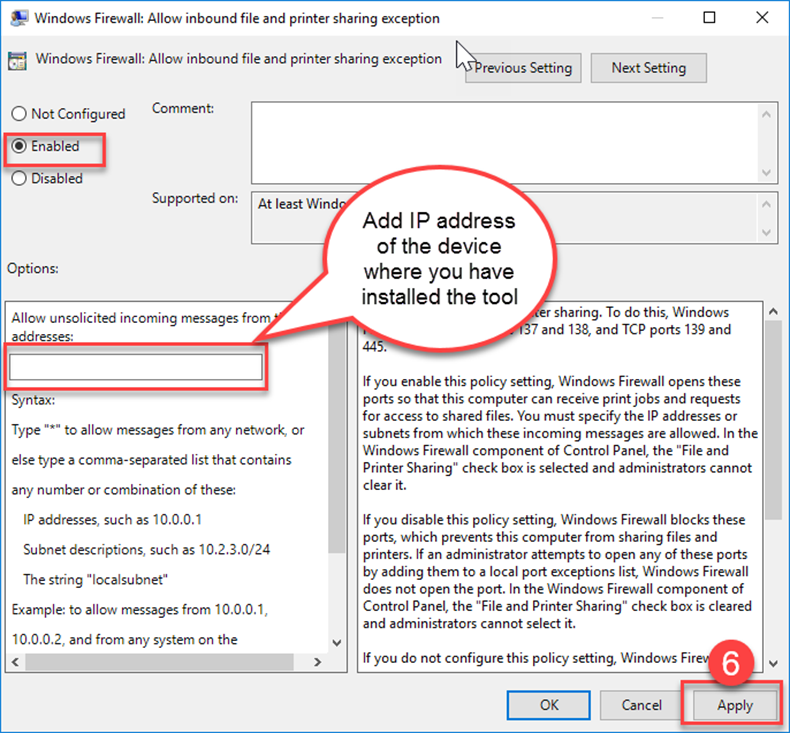
- Double-click Allow inbound file and printer sharing exception.
- Select Enabled.
- Enter the IP address of your Block 64 server or Virtual Appliance.
- Click Apply and OK.
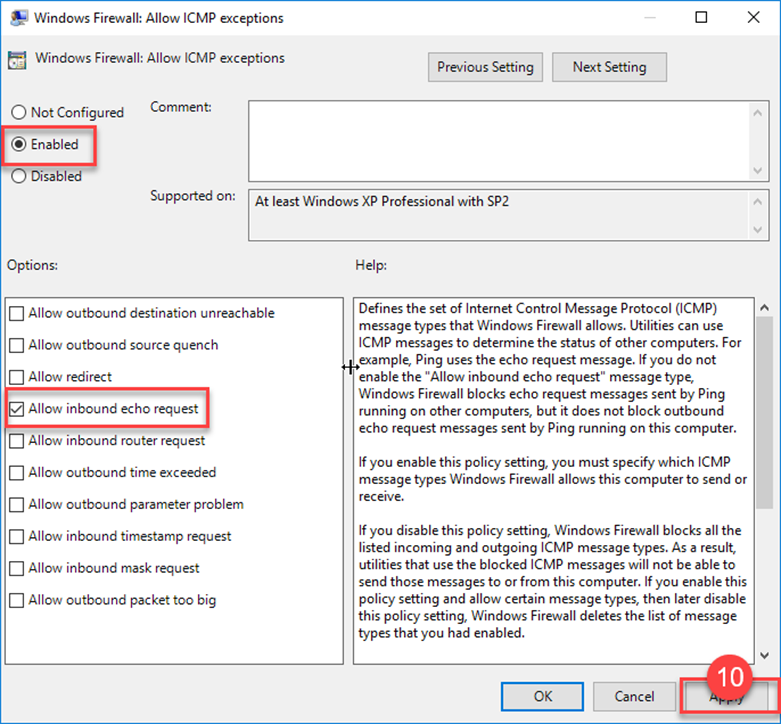
2. Configure ICMP Exceptions
- Double-click Allow ICMP exceptions.
- Select Enabled.
- Check Allow Inbound Echo Request.
- Click Apply and OK.
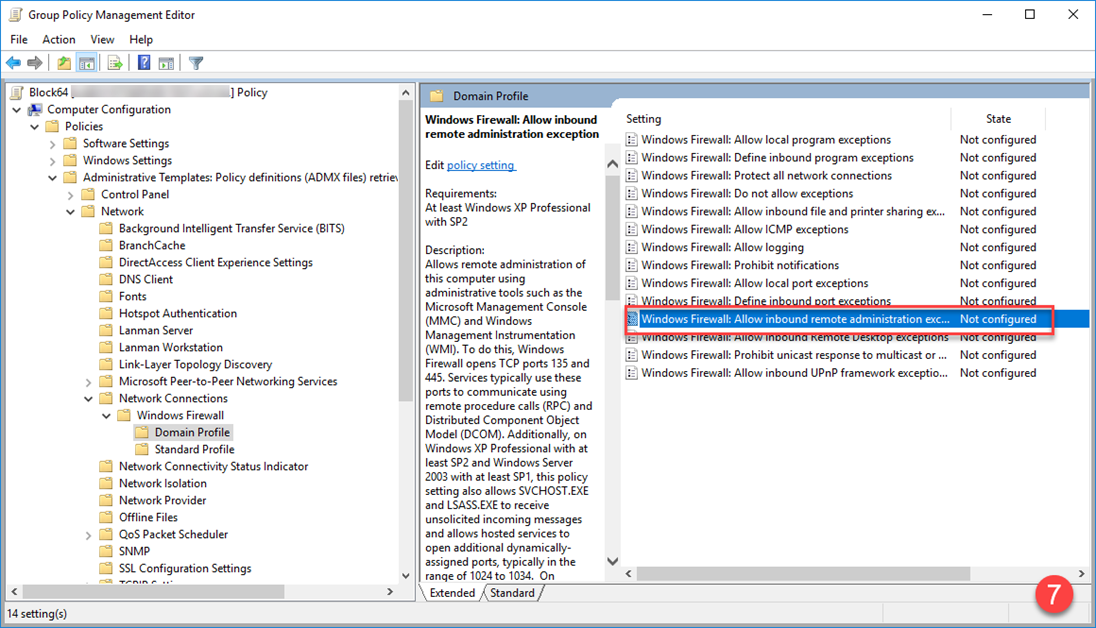
3. Configure Remote Administration Exception
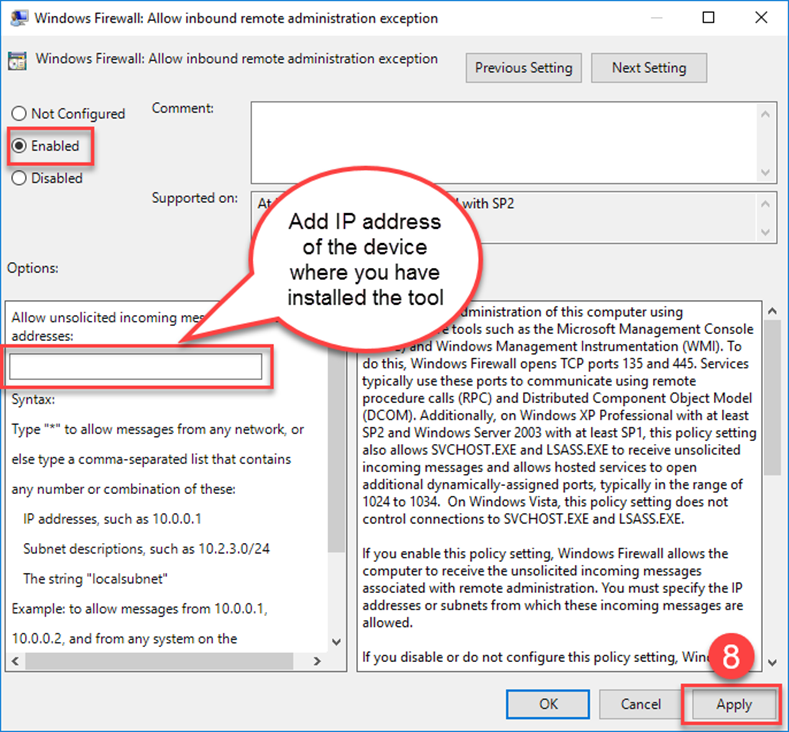
- Double-click Allow inbound remote administration exception.
- Select Enabled.
- Enter the IP address of your Block 64 server or Virtual Appliance
- Click Apply and OK.
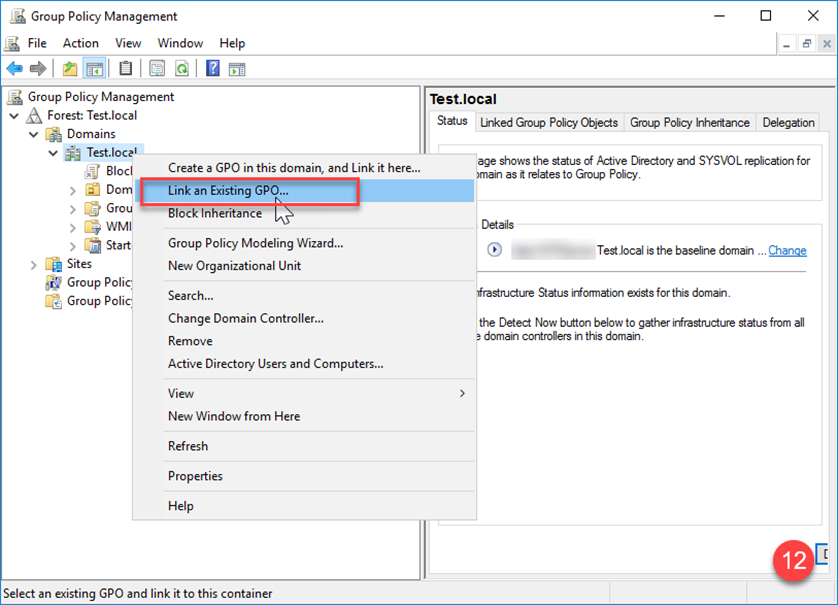
Apply and Verify
- Ensure the GPO is linked to the appropriate domain level.
- Right-click the GPO and select Enforce to ensure the policy is applied.
(Optional) Enable Remote Registry
If you encounter issues related to Remote Registry, such as inconsistent WMI/RPC behavior or explicit Registry (RREG) errors you can optionally enable the Remote Registry service through the same GPO to help address those cases.
Edit the GPO
- Right-click the same GPO → Edit.
- Navigate to:
- Computer Configuration → Policies → Windows Settings → Security Settings → System Services
Configure the Remote Registry Service
-
In the right pane, locate Remote Registry.
-
Double-click Remote Registry.
-
Check Define this policy setting.
-
Configure:
-
Startup mode: Automatic
-
Service action: Start service
-
Enabling the Remote Registry service can introduce additional exposure if not properly controlled. Although Block 64 only performs read-only queries, the service itself allows remote access to the Windows Registry. It’s recommended to scope this GPO appropriately and disable the service if it is not needed after troubleshooting.
Wait for the GPO to propagate. To force an immediate update, in Command Prompt (CMD) run the following command on any device: gpupdate /force
Verify GPO application using: gpresult /v
-
- Make sure you open CMD as an administrator before running
gpresult /vto obtain full results.
- Make sure you open CMD as an administrator before running
If you need to enable the WinRM service for endpoint inventory, please refer to our WinRM GPO Documentation
Refer to the screenshots below for detailed guidance:
GPO Settings: Configuration Details
This GPO's effects apply directly to the IP address specified in its configuration, whether it belongs to the device hosting the application or the virtual appliance running Blockbox. It impacts the communication between the application or appliance and the network devices it attempts to connect with.
Allow Inbound File and Printer Sharing Exception
- Purpose: Enables the Block 64 server to receive information about installed software using file and printer sharing protocols.
- Effect: Allows inbound requests from the Block 64 server through the Windows Firewall.
- Details: Typically uses TCP ports 445 (SMB) and 139 (NetBIOS)
- Purpose: Allows remote management capabilities for more detailed hardware and resource data collection.
- Effect: Permits remote administration traffic from the Block 64 server.
- Details: Utilizes TCP ports 135, 1025-5000, and 49152-65535 for Remote Procedure Call (RPC).
- Purpose: Enables Block 64 to send ping (ICMP) requests to assess device availability and connectivity.
- Effect: Improves device monitoring and troubleshooting.
- Details: Allows ICMP echo requests without exposing other ports.
Enable Remote Registry
- Purpose: Allows the Block 64 Appliance or Discovery Application to remotely read required Windows Registry keys when devices return RREG errors or when registry data cannot be retrieved via WMI/RPC.
- Effect: Enables the Remote Registry service so the Block 64 server can securely read registry values needed for hardware, software, or configuration inventory.
This does not modify the registry; it only enables the remote read capability.
-
Details: Uses the built-in RemoteRegistry service over standard management channels (WMI/RPC). Disabled by default on many endpoints, which can result in registry-related inventory errors.
