Security - Endpoint: Software Vulnerabilities
Insights - Software Vulnerabilities Report
Overview
The Software Vulnerabilities report provides an in-depth analysis of the security risks posed by outdated or vulnerable applications within an organization’s IT infrastructure. It empowers IT and security teams to detect, assess, and address software vulnerabilities proactively, minimizing the risk of exploitation by cybercriminals.
Outdated or unpatched software is one of the most common entry points for cyberattacks. This report plays a crucial role in safeguarding an organization's digital assets by identifying weaknesses within its software ecosystem. It helps organizations to:
-
Recognize and evaluate the risks of known software vulnerabilities.
-
Assess the number of endpoints affected by vulnerable software versions.
-
Focus remediation efforts on critical vulnerabilities to minimize impact.
-
Prioritize updates based on severity levels (Critical, High, Medium, Low).
-
Ensure compliance with security regulations and strengthen defenses.
Details of the Report
The Software Vulnerabilities report consolidates vulnerability data into visual and tabular formats, providing actionable insights for faster decision-making.
This report can be found in the following path:
Reports > Security > Endpoint Security > Software Vulnerabilities
Key Metrics
The report highlights the following:
-
Top Vulnerable Products – A bar chart showing applications with the highest number of vulnerabilities and affected devices.
-
Total Vulnerabilities – The overall count of detected software vulnerabilities.
-
Affected Devices – The number of endpoints impacted by each vulnerable product.
-
Severity Level – Classification of vulnerabilities (Critical, High, Medium, Low) based on CVSS industry standards.
What Can Be Found in the Report
The detailed data section provides a sortable table with the following columns:
-
Publisher – The developer or publisher of the vulnerable software.
-
Product – The name of the software application.
-
Version – The vulnerable version currently detected.
-
Vulnerabilities – The number of vulnerabilities associated with the version.
-
Affected Devices – How many devices are running the vulnerable version.
-
Severity Level – The CVSS-based severity rating (Critical, High, Medium, Low).
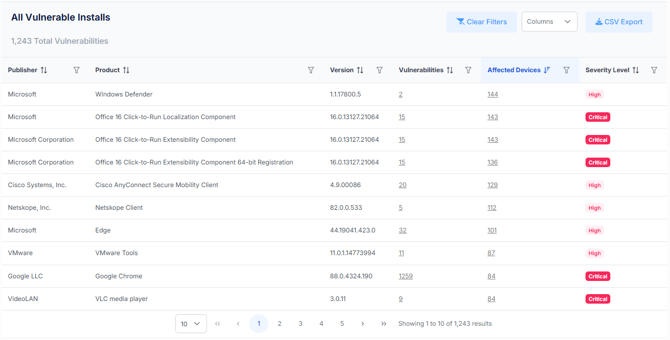
Additional features include:
- Filters and Column controls to refine data views.
- CSV Export for external reporting and analysis.
How This Report Can Help Your Business
By regularly reviewing the Software Vulnerabilities report, organizations can:
-
Strengthen security by identifying and patching vulnerable software quickly.
-
Minimize cyberattack risks by prioritizing updates for critical and high-severity vulnerabilities.
-
Maintain compliance with security frameworks and industry regulations.
-
Optimize patch management efforts by focusing on the most impactful risks.
-
Improve overall resilience and reduce exposure to known threats.
This report is powered by Block 64 tools, which continuously monitor installed software, versioning, and vulnerability databases to detect risks in real time. By regularly acting on these insights, organizations can maintain a proactive security strategy, minimize exploitation risks, and support stable, secure IT operations.

