Security - Endpoint: Endpoint Vulnerabilities
Insights Reporting - Endpoint Vulnerabilities Report
Overview
The Endpoint Vulnerabilities report provides a comprehensive analysis of security risks associated with endpoint devices in an organization's IT environment. It helps IT and security teams monitor vulnerabilities, track devices running end-of-life (EoL) operating systems, and detect endpoints lacking antivirus (AV) protection. By leveraging these insights, organizations can proactively mitigate threats before they impact business operations.
Endpoint security is a critical aspect of an organization's cybersecurity strategy. This report allows organizations to:
-
Identify and assess security vulnerabilities affecting endpoint devices.
-
Monitor devices that are approaching or have surpassed their manufacturer-supported lifecycle.
-
Detect endpoints missing essential AV protection to reduce exposure to malware and cyber threats.
-
Ensure compliance with security frameworks and regulatory requirements by maintaining secure endpoint configurations.
Details of the Report
The Endpoint Vulnerabilities report consolidates data on endpoint security risks, providing actionable insights to enhance device security and compliance. It includes key security indicators that allow IT teams to prioritize and address vulnerabilities efficiently.
This report can be found in the following path:
Reports > Security > Endpoint Security > Endpoint Vulnerabilities
Key Metrics
The report includes the following key metrics and visualizations:
-
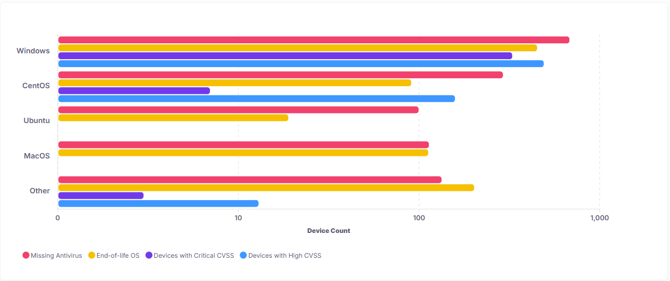
Missing Antivirus – Devices without up-to-date antivirus protection.
-
End-of-Life OS – Devices running operating systems that are no longer supported by the manufacturer.
-
Devices with Critical CVSS – Devices with software installations affected by vulnerabilities rated Critical by CVSS scoring.
-
Devices with High CVSS – Devices with software installations affected by vulnerabilities rated High by CVSS scoring.
A bar chart displays these risk categories by device operating system (Windows, CentOS, Ubuntu, macOS, and Other). This helps teams quickly identify where the largest concentrations of risk exist.
What Can Be Found in the Report
The detailed data section provides a sortable table with the following columns:
-
Device – The endpoint hostname or identifier.
-
Endpoint Risk – The calculated risk level (e.g., Critical, High).
-
Missing Antivirus – Shows if the device is missing AV protection.
-
End-of-Life OS – Indicates whether the device OS is unsupported.
-
Installs with Critical CVSS – Count of installations with Critical vulnerabilities.
-
Installs with High CVSS – Count of installations with High vulnerabilities.
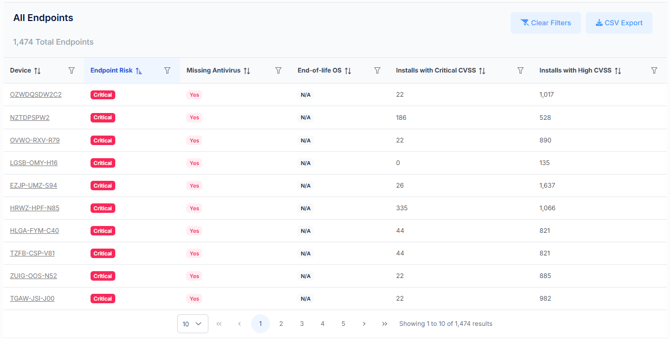
Filters and CSV Export are available to refine the view or extract data for external analysis.
How This Report Can Help Your Business
By utilizing this report, organizations can:
-
Strengthen endpoint security by identifying and addressing vulnerabilities proactively.
-
Reduce compliance risks by ensuring endpoint devices meet security standards.
-
Prevent breaches by monitoring antivirus compliance across all devices.
-
Optimize IT asset lifecycle management by identifying aging devices and planning replacements.
-
Enhance overall cybersecurity resilience by maintaining visibility into endpoint risks.
The Endpoint Vulnerabilities report is generated using data from the Block 64 tools. It aggregates information from Software Vulnerability Databases, Device Lifecycle Data, and Antivirus Compliance Checks.
By regularly reviewing this report and acting on its insights, organizations can improve their cybersecurity posture, maintain compliance, and reduce exposure to potential threats.
